The digitized ecosystem looks alluring to entrepreneurs and business owners. As an organizational head, you’d be keen to switch to the virtual business paradigm. While you brace to exploit the advantages of networking virtually and expanding your client base beyond domestic boundaries, have you drawn your line of defense against cyber threats?
With this risk quotient looking increasingly menacing, how resilient do you think your business is to cyber threats? Do you know that every 39 seconds a cyber attack takes place? On average, businesses lose $9.44 million following a security breach. Predictions reveal that in 2023, cybercrime is going to cost global companies as much as
$8 trillion!
Ransomware attacks, malware, phishing attacks, and a plethora of new attack modules threaten to jeopardize your operations. Protecting your business from cyber threats is the need of the hour.
Before recommending effective ways to secure your business from online attacks, we’d like to present some statistics.
Top Cybersecurity Statistics Business Owners Should Know
- Gartner reveals that global businesses would be spending $188.336 billion on risk management and information security.
- 52% of malware can bypass network security by using USB drives.
- In 2023, the financial industry witnessed a massive 1300% increment in ransomware attacks.
- 43% of cyberattacks are targeted at small businesses.
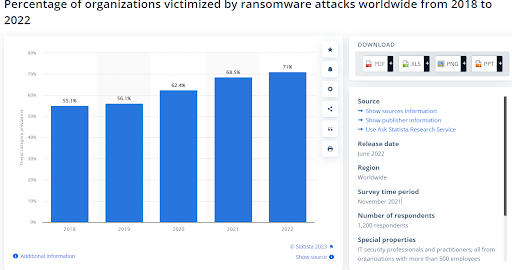
- In 2022, 71% of the targeted businesses became ransomware victims.
The graph reveals the percentage of business organizations falling prey to ransomware attacks between 2018 and 20222. The trend looks increasingly menacing, with the percentage rising to 71% in 2022 from 55.1% in 2018.
What Are The Most Common Cyber Threats In 2023?
Most businesses remain susceptible to the following cyber threats in 2023 with a high-risk profile.
1) Malware
Cybercriminals are designing many as 300,000 new malware per day! Besides, the culprits choose email to deliver 92% of malware.
Malware refers to any malicious tool like worms, viruses, ransomware, and spyware. When any of your employees unknowingly click on a malicious attachment or link delivered through email or social media platforms, they affect your system. Once activated, malware can disrupt your operations in several ways. These include:
- Installing harmful tools in the background
- Blocking access to resources or data
- Rendering the system inoperable by disrupting parts
- Stealing crucial business information from your drives
2) Social Engineering Frauds
Rather than exploiting technical loopholes, cybercriminals take advantage of human weaknesses through social engineering frauds. This type of cyber threat involves manipulating your staff or employees so that they end up divulging confidential business information.
Commonly, cybercriminals send phishing links through emails. They turn out to be imposters and replicate legitimate organizations or authorities. Cybercriminals also exploit human vulnerabilities to steal credit card information, social security numbers, and account passwords.
3) Man In The Middle Attacks
A MITM (man-in-the-middle) attack takes place when cybercriminals intervene in a transaction between two parties. Such cyber threats disrupt traffic and steal data during transit.
The key vulnerability that renders your organization susceptible to MITM is an unsecured Wi-Fi network. After placing themselves between the network and the visitor, cybercriminals install software using malware for unauthorized data access.
4) SQL Injection
An SQL (Structured Query Language) injection is an attack module where cybercriminals integrate your server using SQL with malicious code. The server starts releasing data when this code is injected. This way, your server could be divulging valuable business information to unauthorized parties and even your competitors.
5) Password Theft
Compromised passwords happen to be one of the most common types of cyber threats. Obtaining account passwords open up treasure troves of data to hackers. Password thefts take place through different attack modules, including social engineering. The attackers capitalize on weaknesses in human interactions and breach security by tricking employees.
How to protect your business from cyber threats?
Now that you are familiar with the most common cyber threats, it’s time to step up your cyber resilience. We have recommended some tried-and-tested tips that should strengthen your line of defense against online attacks.
1) Educate your employees
Given that 9 out of 10 cyberattacks have a human error at the root, training your employees would help your organization combat cyber threats. Cyber-vigilant staff happens to be the best resource against any kind of online threat. Organize training sessions for your workforce as a part of your continuous learning modules. This ensures that all your employees should know:
- The ideal way to treat official information and resources both at the workplace and at home
- How to adhere to security policies and practices like configuring strong passwords
- How to handle emails and identify unsolicited mails
- The immediate course of action in case of a security breach
- How to secure valuable data and stick to your information-use policy
From time to time, dispatch newsletters to your employees and carry out ongoing training to cultivate a cyber-resilient culture.
2) Secure your networks and databases
These guidelines will help you revamp your line of defense to secure your databases and networks.
- You may consider seeking managed security services to mitigate cyber threats. This way, cybercriminals wouldn’t be gaining unauthorized access to your business information.
- Conceal your Wi-Fi network and secure the same using a strong password.
- Store selective information in your business database. Usually, organizations store their documents and crucial data centrally in these databases. Secure this virtual storage to ensure better cybersecurity.
- Configure automatic backup of your databases twice a week, or even daily. This implies that you won’t end up compromising vital business information in case of a ransomware attack or any other security breach.
3) Install firewalls in your system
Firewalls go a long way in securing your system from hackers. All your employees, including those working, remotely should remain secure under firewalls. Even if your employees are using a VPN (virtual private network) or rely on a CSP (cloud service provider), installing firewalls is a must.
To take your security against cyber threats to the next level, install an IDPS (intrusion detection/prevention system).
4) Regulate data security while payment processing
Potential cyber threats include credit card fraud. To mitigate this risk from financially jeopardizing your organization, work with established payment processing platforms and reputed banks. These organizations should use only validated and trusted tools to keep credit card fraud at bay.
Established eCommerce platforms such as
Ubuy India have already demonstrated their cyber resilience in this regard. Considering the online threat potential, eCommerce brands must have SSL certificates and partner with reputed payment gateway providers.
5) Create best practices to combat cyber threats
Establish strict policies and best practices for your employees to combat cyber threats. For instance, every organization should have policies that require their employees to:
- Set strong passwords and change them at regular intervals
- Handle customer data responsibly and secure the same
- Use MFA (multi-factor authentication) while setting accounts and passwords
- Isolating compromised systems to prevent malware from affecting the entire network
- Handle hardware responsibly and dispose off old components securely
Hardware components such as cell phones and laptops turn out to be common targets for information theft. While disposing away old hardware, destroy the information to keep your data secure.
6) Secure your wireless networks and access points
The best way to keep cyber threats like MITM and SQL injection at bay is to secure your wireless networks and access points. Have a look at the best practices in this regard.
- Configure your wireless access point in such a way that the system doesn’t broadcast its SSID
- Use WPA-2 (Wi-Fi Protected Access 2) on your router with AES (Advanced Encryption Standard) to ensure secure data encryption
- Each time you install a new device, set a different administrative password
- Refrain from using Wired-Equivalent Privacy (WEP)
- Businesses providing their clients with wireless internet access should separate this system from their commercial network
7) Use email and web filters
One of the effective measures to manage cyber threats is to install web and email filters. This way, you can prevent culprits from clogging the inboxes of your employees with spam content. Many cyber-resilient organizations are using ‘blacklisting’ services to mitigate these threats. This way, you can prevent your employees from accessing risky websites containing malware.
Apart from this, spread a word of caution among your workforce to refrain from accessing sites that are associated with cyber threats. Even a single employee accessing these sites can jeopardize your network. Using web filters, therefore, serves as a reliable defense against such vulnerabilities.
8) Update your software and systems
Make sure that your security software, antivirus, and operating systems are updated regularly and automatically. Updated systems are robust and draw a better line of defense against cyber threats. This enables businesses to patch their security flaws and address the vulnerabilities that cybercriminals aim to exploit.
Don’t overlook the update prompts of your firewalls. These shields serve as a gatekeeper of your incoming as well as outgoing web traffic. Keep your firewalls and other security system updated to remain cyber-resilient.
9) Use passphrases instead of passwords
Remember, weak passwords amount to as much as 81% of data breaches in business organizations.
Cybersecurity experts recommend configuring passphrases rather than passwords. Particularly, if any of your accounts contain sensitive business data, passphrases can strengthen your online security.
A secure passphrase contains a minimum of 14 characters. Combine special characters along with numerical figures, and alphabets both in the upper and lower cases. This makes it unpredictable and stronger than passwords.
10) Have a comprehensive monitoring system in place
As a business owner, it’s imperative to track all your hardware, software, and business equipment that remains susceptible to cyber threats. Do away with sensitive data from any system that you are no longer using. Remember, unused or older equipment that you don’t usually update serves as a backdoor for cybercriminals.
Also, make sure that your ex-employees no longer have access to these resources. This reduces the possibility of internal sabotage.
11) Back up your data
Having multiple databases and backups defines your preparedness to deal with cyber threats like ransomware attacks.
Regardless of how vigilant your employees are, cyber threats continue to be a menace. Why not have a plan B in place, anticipating the worst? Create a backup for your database and store them in multiple locations, both online and offline. These include:
- The HR files of your organization
- Business and marketing databases
- Financial and accounting databases
- Payments and accounts receivable files
- Contract documents and other information
Also, inspect your backup regularly to ensure that you can retrieve information from these sources whenever needed. Having multiple databases and backups defines your preparedness to deal with cyber threats like ransomware attacks.
12) Restrict employee access
Not all your employees are authorized to access crucial data in your organization, right? Why not restrict employee access to valuable information and thereby reduce the possibility of human errors? Only authorized and selective employees should gain access to information resources that prove vital for their operations.
As a part of your data security policy, make sure to take protective actions whenever an employee leaves your organization. Delete exclusive accounts and change passwords, besides collecting entry keys and ID badges of your organization from these people.
13) Encrypt sensitive business information
As a countermeasure against cyber threats, secure your smartphones, tablets, and PCs using full-disk encryption. Through encryption, you can convert sensitive information into a code before you send it to the recipient over the internet. To prevent MITM attacks, it’s imperative to encrypt information. This would limit data access only to authorized parties having the encryption key.
Therefore, unauthorized parties wouldn’t gain access to your data while it is in transit. Besides, some sophisticated encryption tools inform the users whether any other party tried to tamper with the data.
Now, securely store a copy of this encryption key away from your business databases in a secure location. While decrypting, the recipients of your emails would require the same key. Remember, never share the key or the password with anyone over email. Try to provide it to them by phone or communicate in any other way.
To step up your line defense mechanism against cyber threats, enter into an agreement with your banking service provider to validate payments only after they meet specified criteria. This would significantly reduce the chances of unauthorized transactions through credit cards.
EndNote
For business owners, prioritizing cyber resilience is of paramount importance. There’s no point in scaling up your venture as long as you remain susceptible to cyber threats. Being a victim of a data breach, ransomware attack, or any type of cybercrime would drain away millions of dollars. The last thing to expect is a reputation loss, which is quite possible if cybercriminals gain access to your customers’ information.
Well, try to be cyber-resilient rather than sorry. With our comprehensive guidelines, you’re now better poised to combat cyber threats and secure your business.
"We value your feedback! Please consider leaving a review on Trustpilot to help us improve our services."
"Did you enjoy your experience with us? Leave a review on Trustpilot and let others know!"
"Your opinion matters to us! Share your experience by leaving a review on Trustpilot."
"Have a moment? Leave a review on Trustpilot and help us serve you better."
"We strive to provide the best experience possible. Please consider leaving a review on Trustpilot and let us know how we're doing."